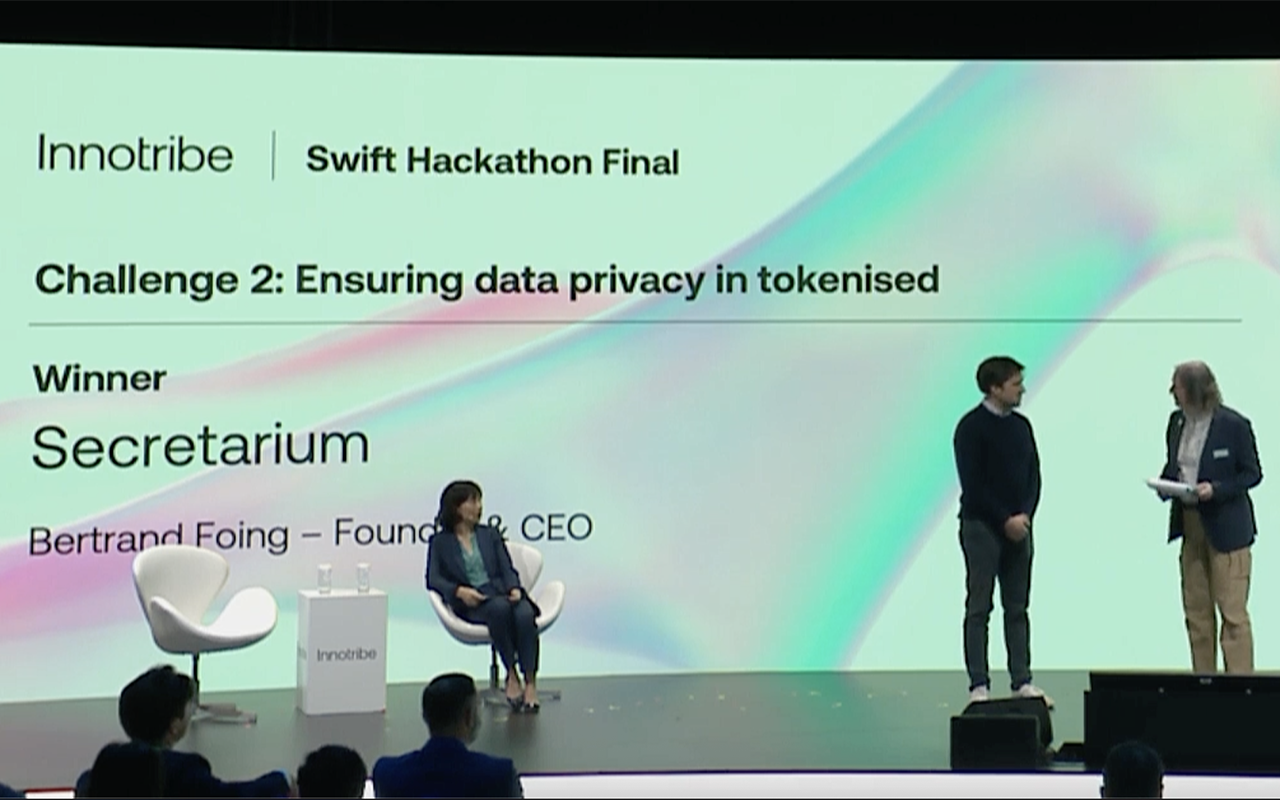
Data Privacy First. Data Security Always.
Guaranteed data protection and integrity for the most critical systems.
Unlocking intelligence from private data
Trustless technology is how we connect sensitive data to secure processing, with no middlemen or blind trust. It empowers data holders to create powerful insights to solve the world’s most complex challenges.
solution for you

Empowering secure data solutions
Secretarium is at the forefront of confidential computing, offering a scalable infrastructure that supports a wide range of use cases.

Self-sovereignty
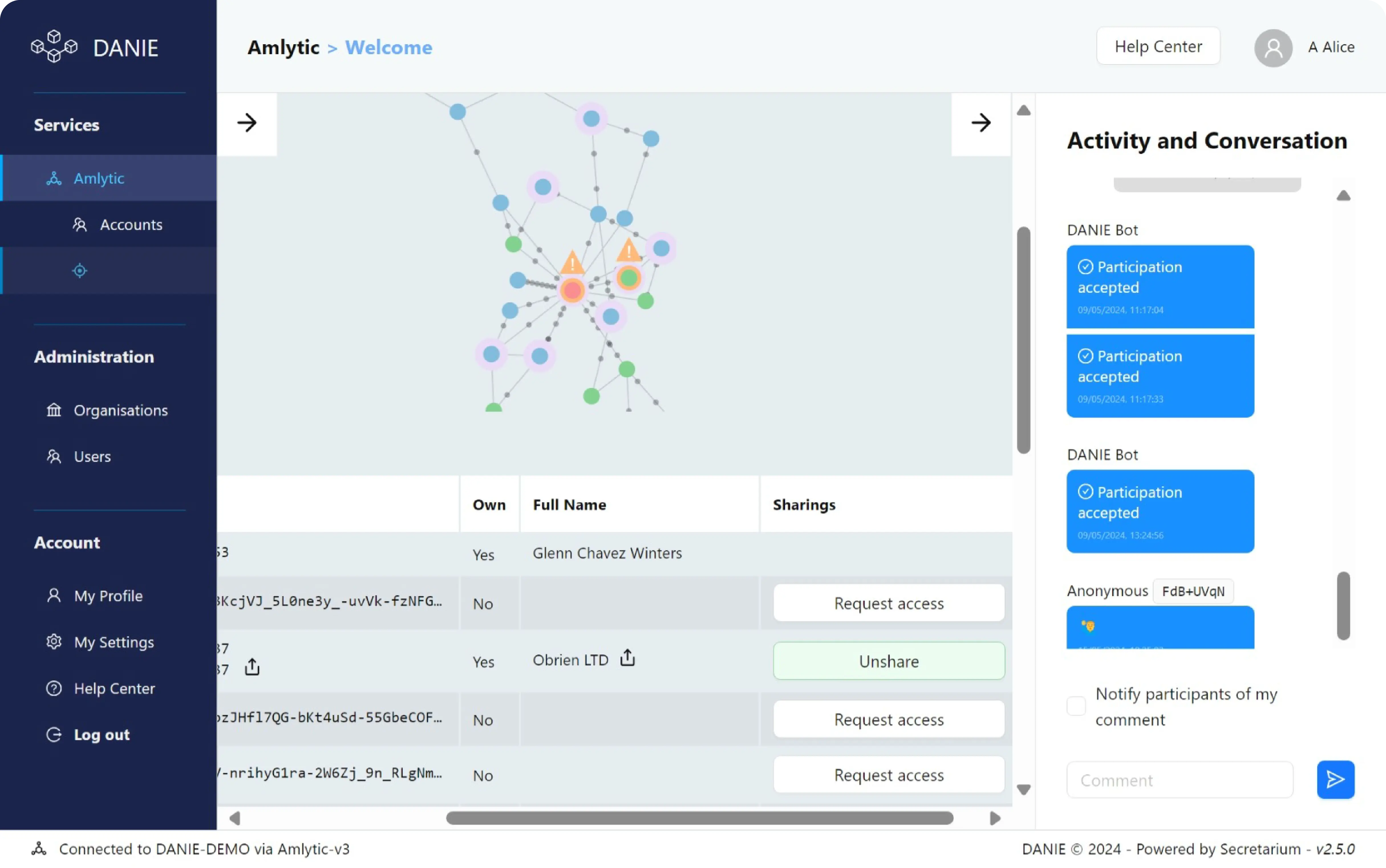
We process data while keeping it always encrypted in memory. No-one has privileged runtime access. Privacy and data ownership is provably preserved.


Verifiable Transparency
Anyone can cryptographically attest the security and privacy guarantees of services hosted by Secretarium. We enforce verifiable transparency, shifting the need to trust a service provider into verifying technical evidences of integrity.


Seamless Security
Our privacy-enhancing technology is designed to support complex use cases with little overhead. A secure and trusted infrastructure should be the norm, not an expensive ideal. Our solution is easy-to-adopt and designed to scale.

Industry Best Partners & Adopters

Our global platform
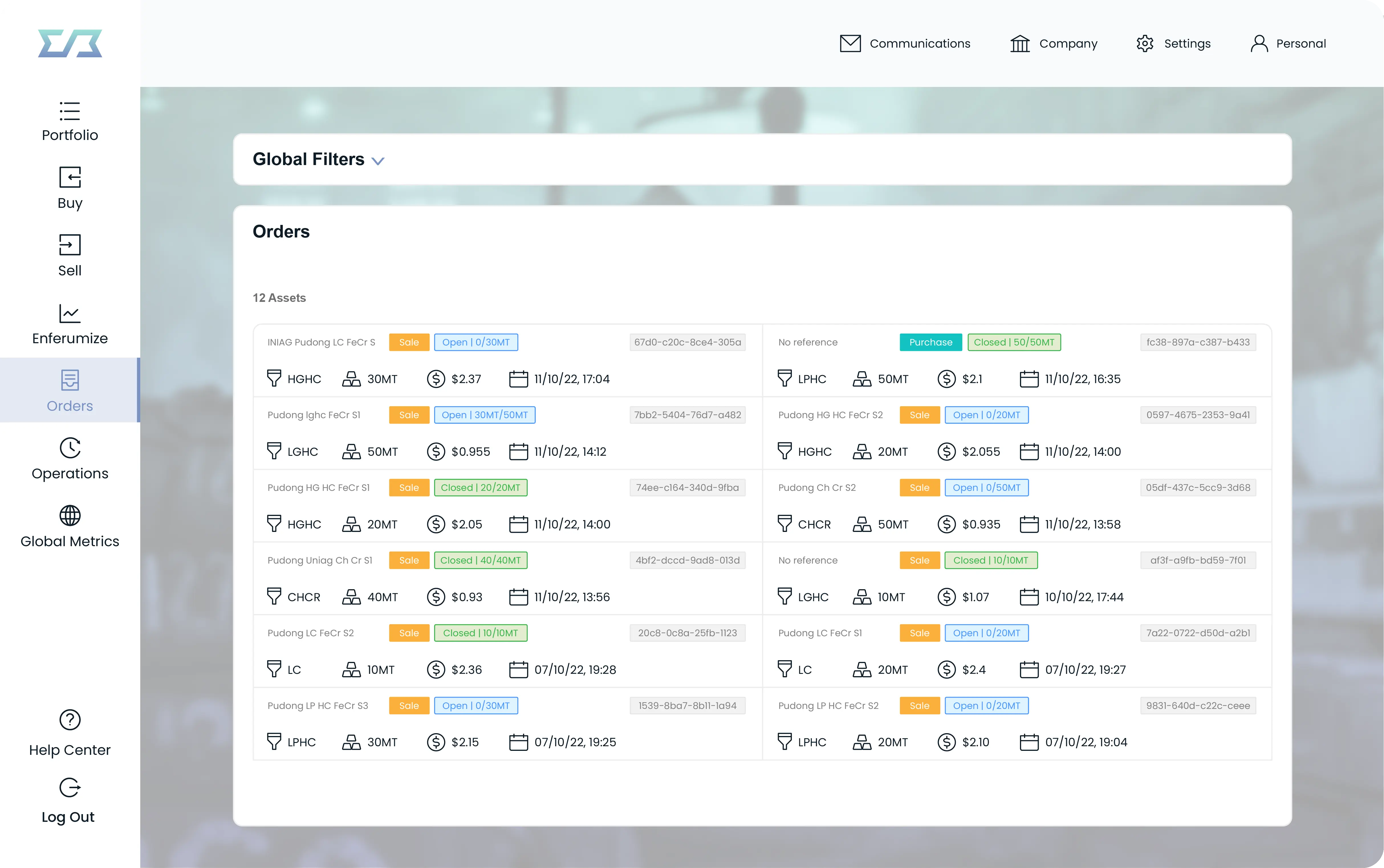
We make building and deploying private applications easy. Focus on your business logic, not infrastructure, with our NoOps platform. Meet compliance requirements effortlessly with built-in data privacy and security features.

Klave is trustless and perfectly aligns with the goals of Web3 decentralisation of powers.

Klave is programmable and allows the deployment of verifiable apps within seconds.

Klave does not require advanced knowledge or skills in cryptography, encryption, or low-level programming languages.
Apps created

Technology
Secretarium proposes a unique scalable approach for secure data processing. Our technology facilitates crossing the trust chasm and unlocks a universe of use cases where privacy is a business driver.
Articles & Publications
We actively engage in highly innovative projects. Explore our latest publications featuring our cutting-edge technology.









.png)


.png)


